While designing any application security is a paramount concern, especially in Cloud where there is not one application, which standalone can solve all Integration needs. We generally use a combination of services for specific operations.
For example – A full-fledged architecture will have multiple components like a few APIs running in Containers, some hosted in Web Apps, while a few using Logic Apps and Function Apps, etc.
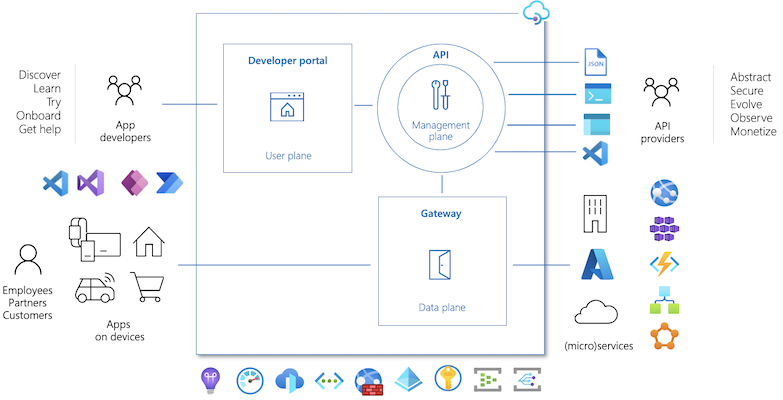
This introduces a need for a centralized interface/gateway to all outside (internal/external) partners. Azure API Management fits this place perfectly.
You can read more about APIM below link –
In short, it provides many benefits like –
- Abstract backend architecture diversity and complexity from API consumers by acting as a facade, accepting API calls and routing them to configured backend services
- Securely expose services hosted on and outside of Azure as APIs, by verifying API keys, JWT tokens and certificates
- Protect, accelerate, and observe APIs and also enforces quotas and rate limits, perform transformation etc. via different policies
- Enable API discovery and consumption by internal and external users
The focus of this blog is to only enable OAuth2.0 for our backend APIs, hosted in Logic Apps, Function Apps or Web App.
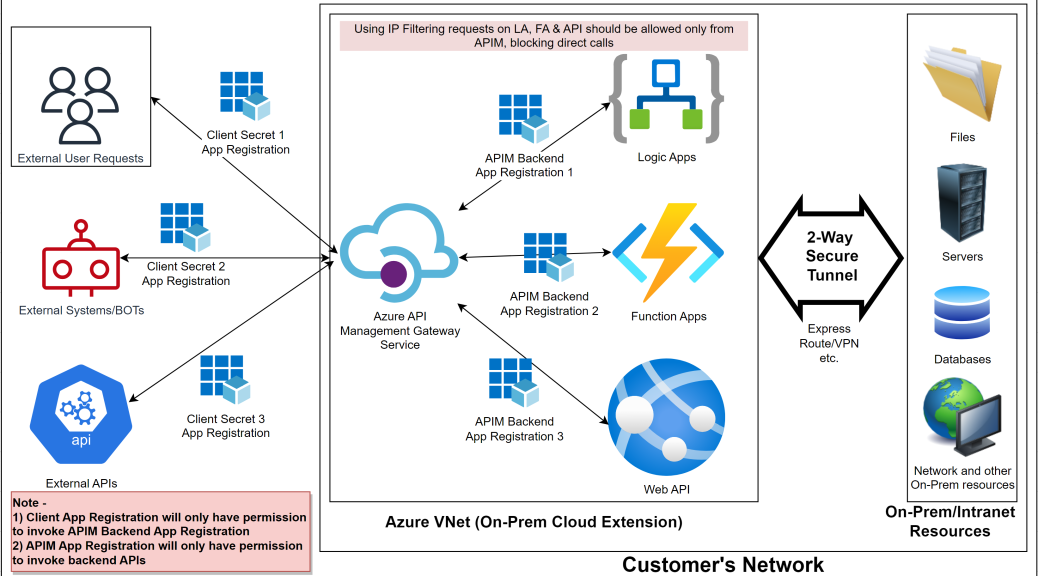
Overall Architecture –
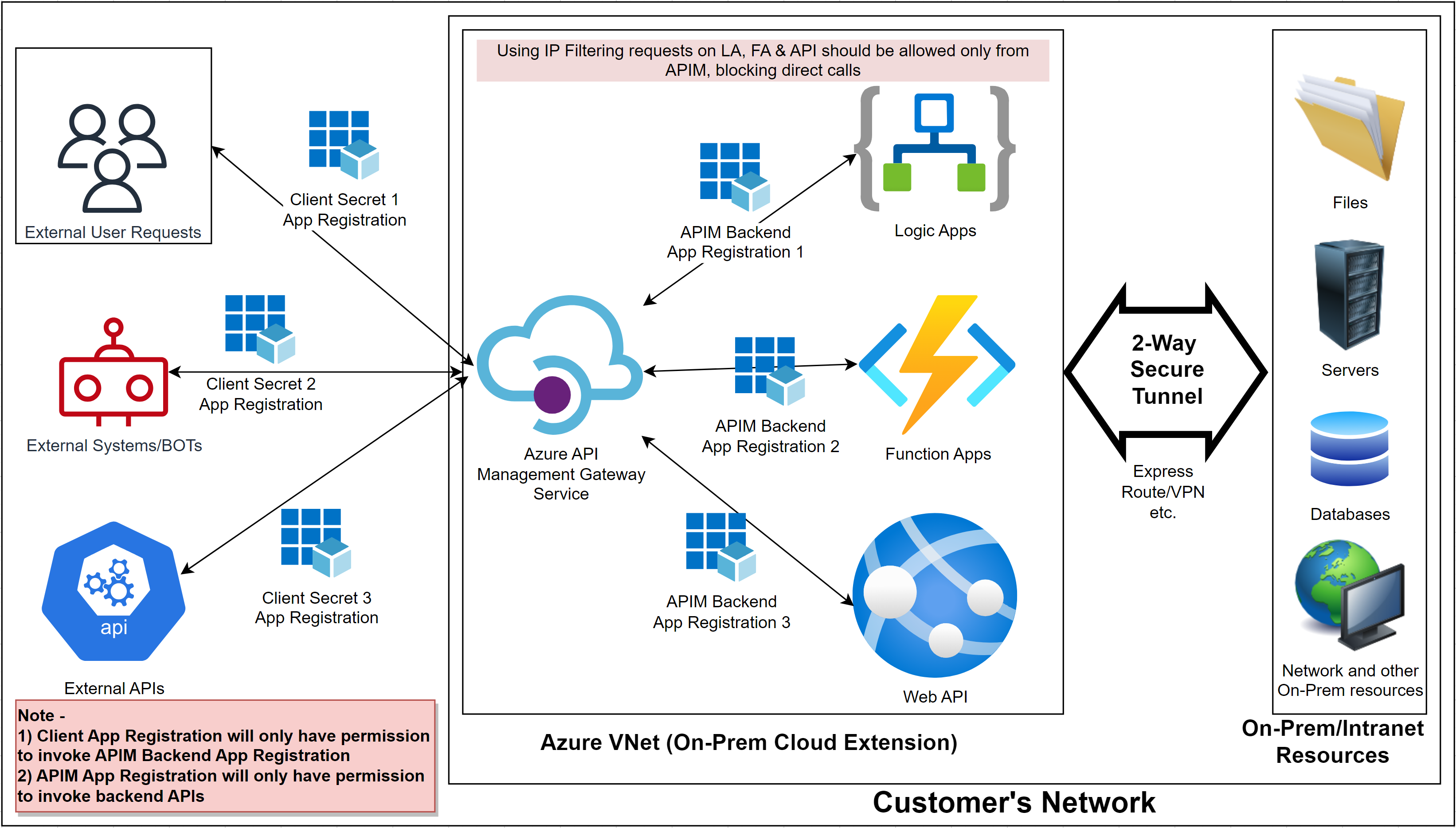
Our Demo environment has below resources
- API Management Service – We used the developer edition
- Logic Apps – Ours is a simple logic app with a request-response operation
- App Registrations mentioned below –
- APIMBackendApp – This App Registration will have permission to invoke backend APIs like Logic Apps, Function Apps, Web API etc.
- DemoClientApp – This App Registration will have very limited permission only enough to call the above App Registration -APIMBackendApp
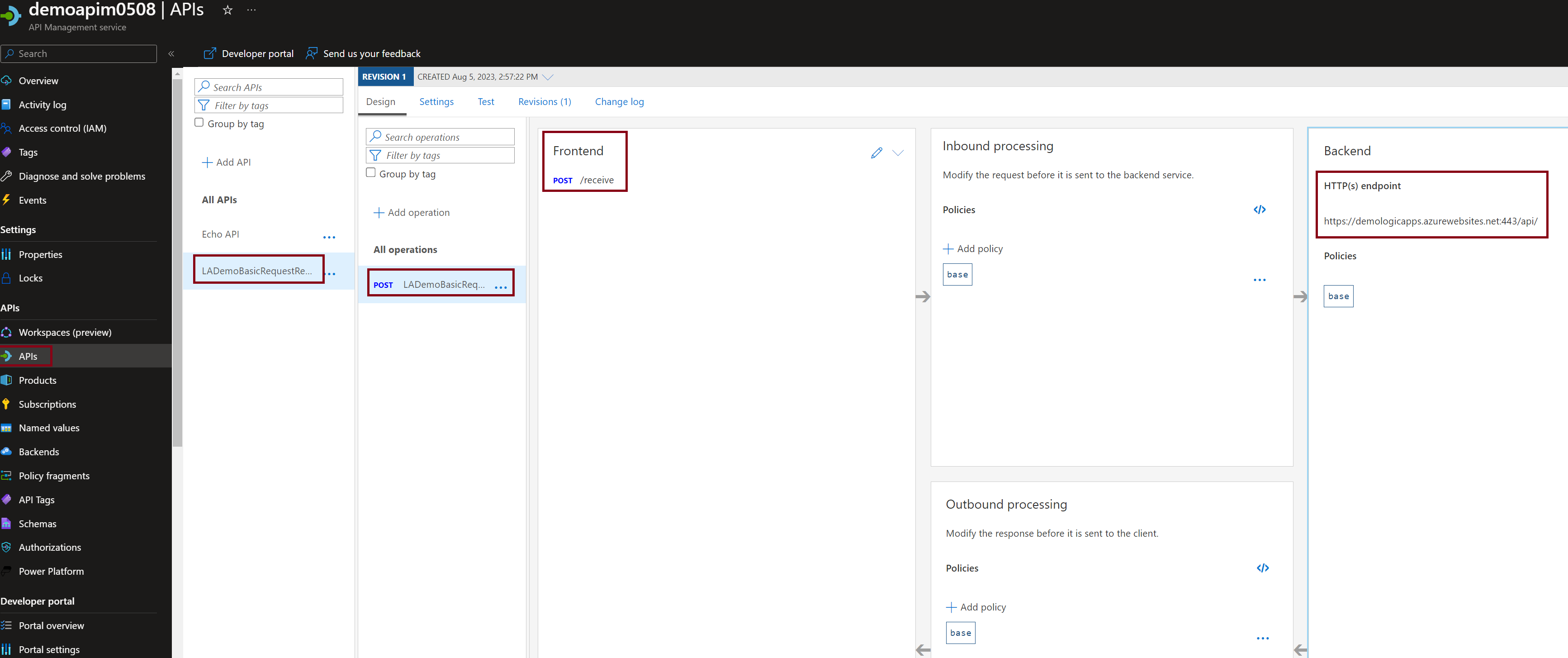
Pre-requisite – A working API configured in APIM. In our demo, I configured the Logic Apps in APIM
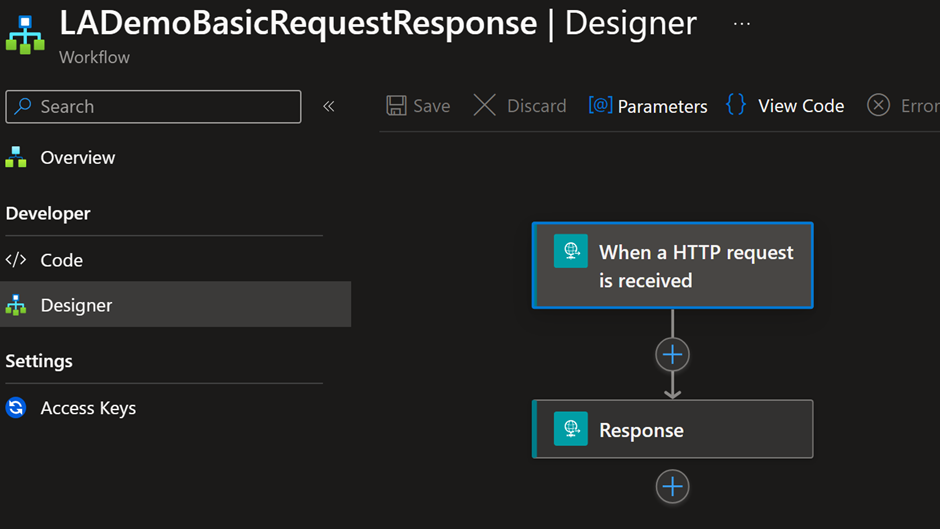
This LA is already configured in APIM as an API. Detailed steps of how to onboard LA to APIM will be covered in another article.
Steps to configure OAuth 2.0 in APIM
- Create App Registration for Backend App and Client App
- Configure OAuth Server in APIM
- Configure Policies in APIM for OAuth token validation
- Test via Postman App
App Registration-> APIMBackendApp
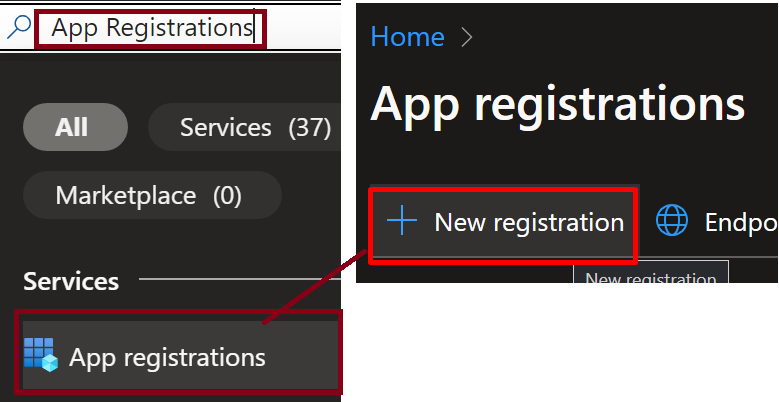
- Go to Azure Portal and Search for App Registration and click on “New registration”
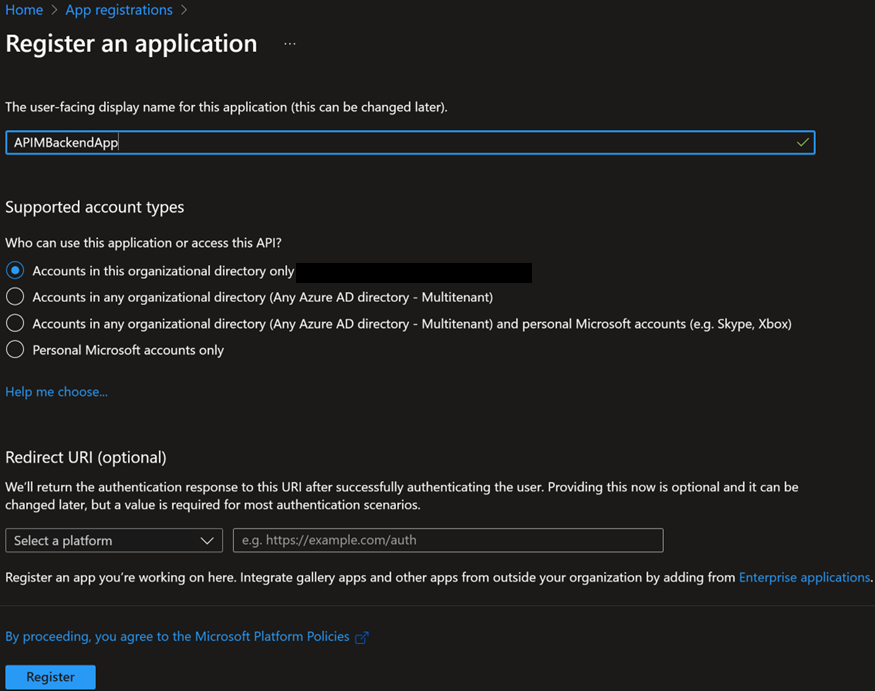
2. Provide the Name and leave everything as default
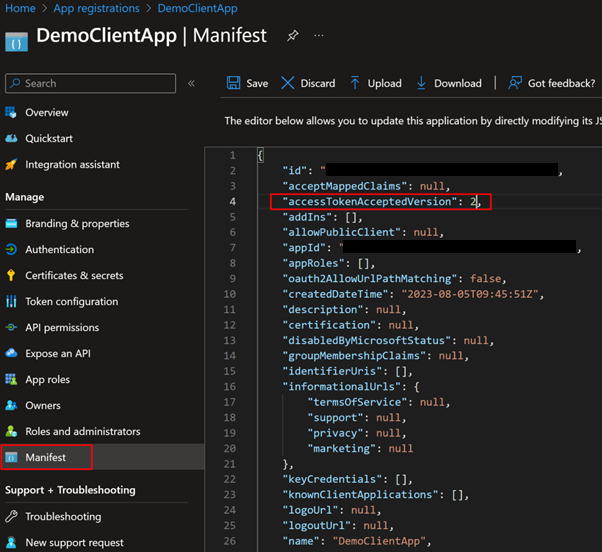
3. First step is to change “accessTokenAcceptedVersion” to 2, to be able to accept OAuth 2.0 tokens. Go to “Manifest” and make the change as shown and make sure to Save

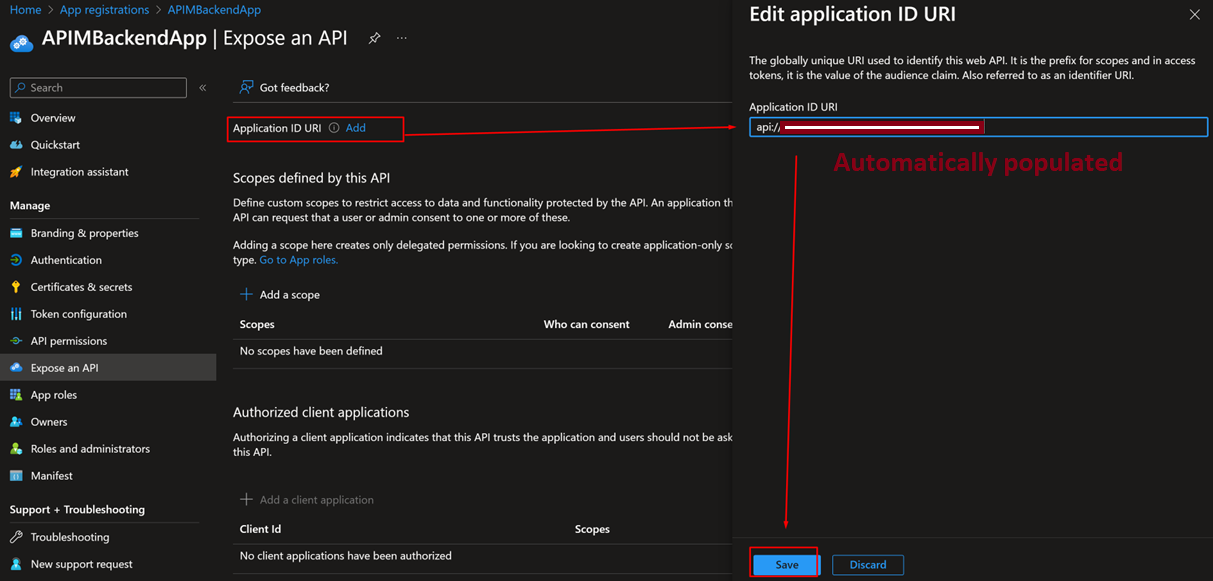
4. Go to “Expose an API” and “Add” an Application ID URI
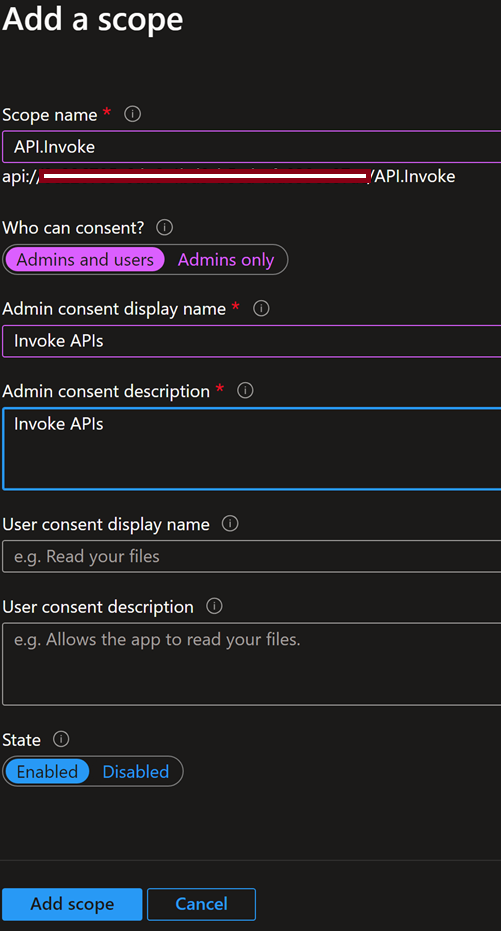
5. Add a scope as shown below
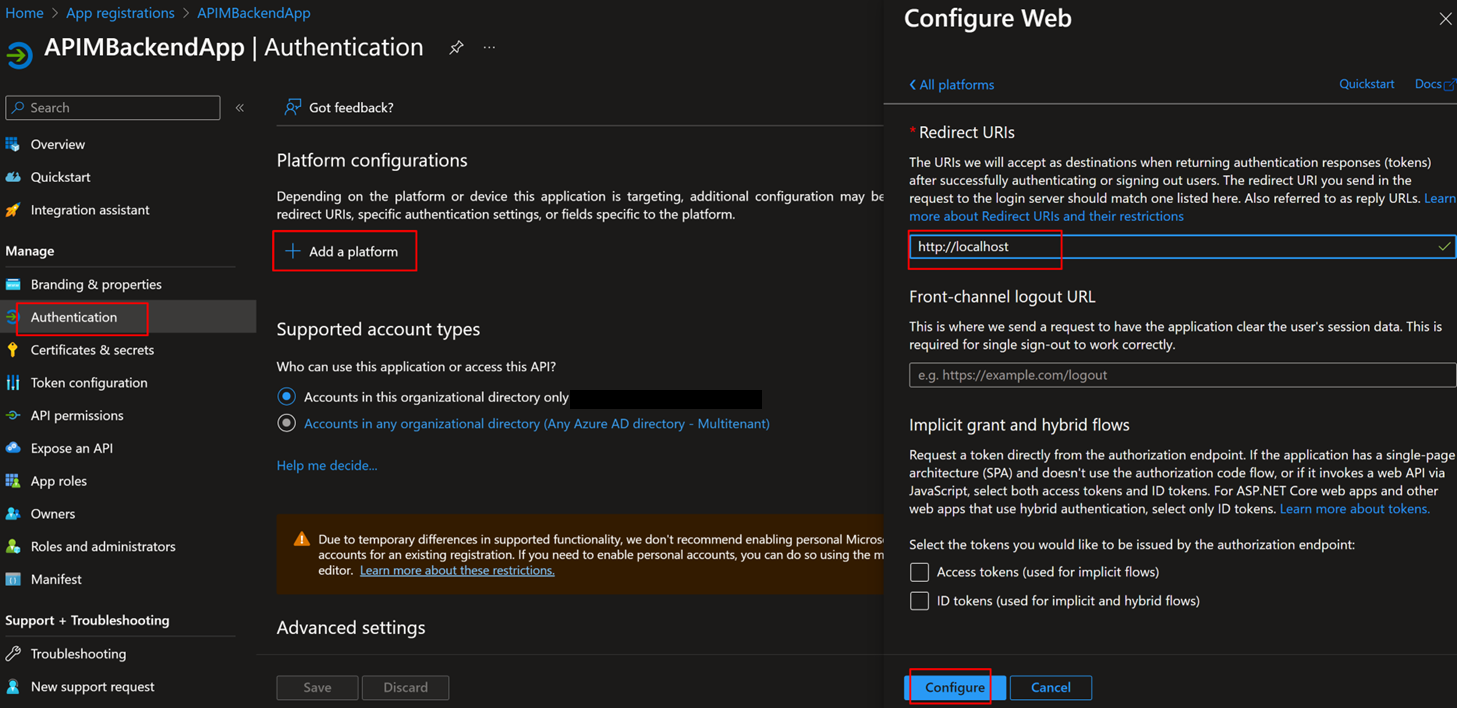
6. Go to “Authentication” => “+ Add a platform” => Configure Web to “http://localhost”
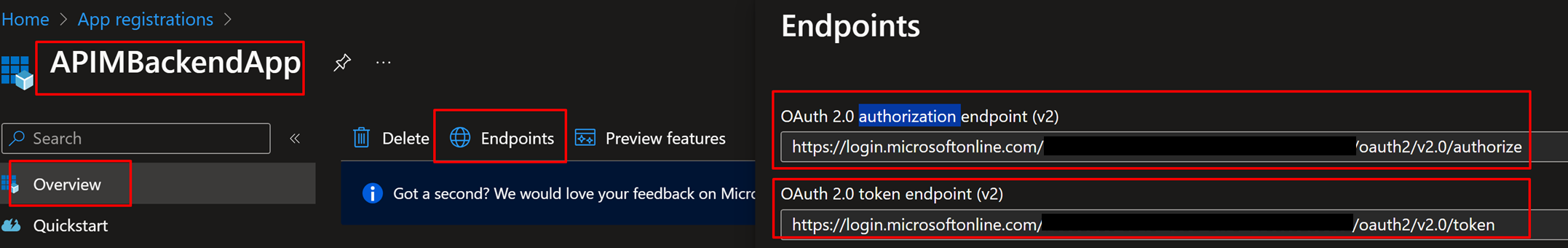
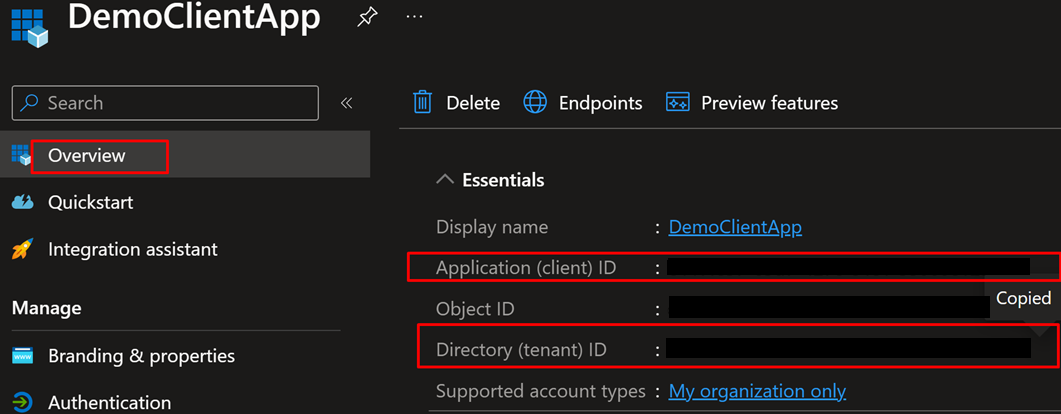
7. Finally, make a note of the below details from the Overview page, to be used later
- OAuth 2.0 Endpoint
- OAuth 2.0 Token Endpoint
- Client ID
- Tenant ID

This completes, APIMBackendApp. now let’s configure App Registration for the Client app

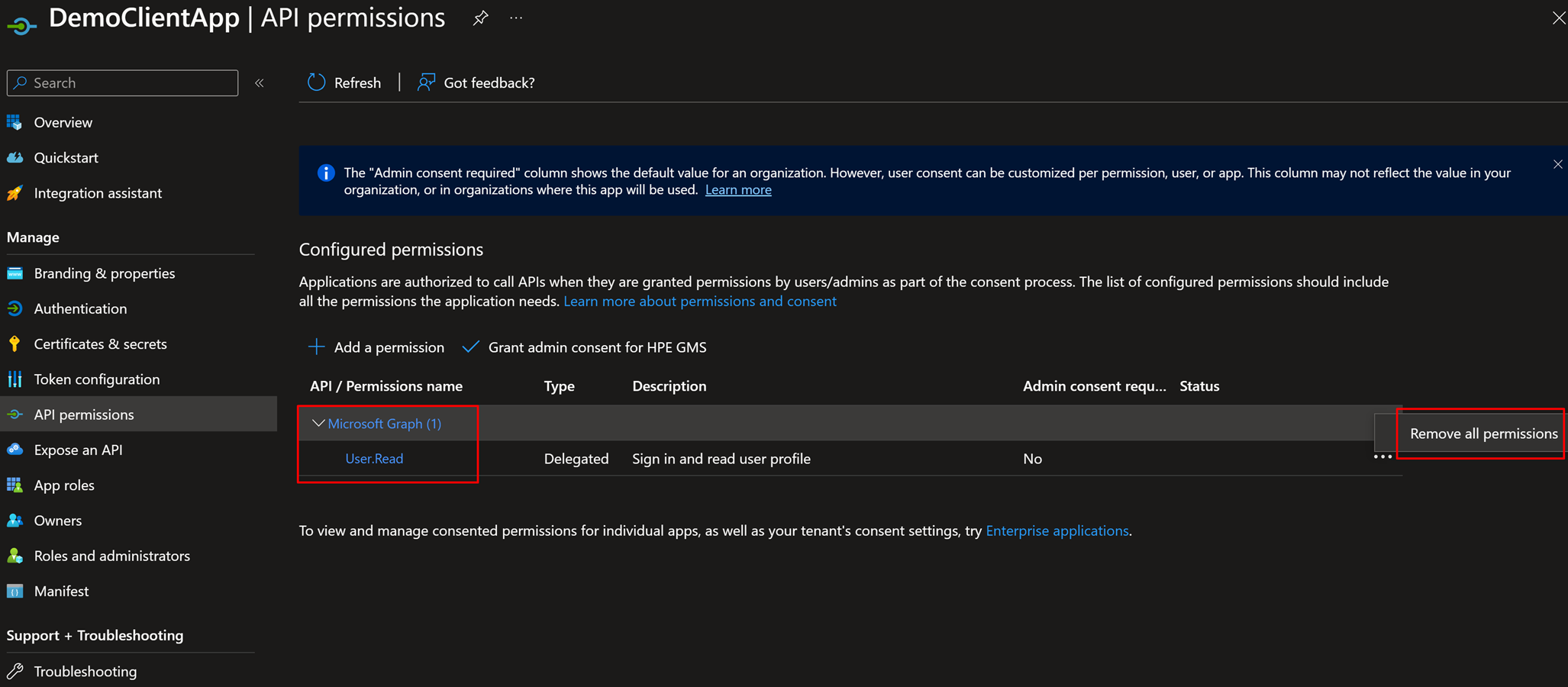
2. Now let’s remove the default permissions to only provide very limited access to be only able to call APIMBackendAppReg. Go to “API permissions” => Remove all permissions.
3. Provide permision to call APIM App reg. Click on “+ Add a permission” => Search for your app registration created above and Add permission as shown below.

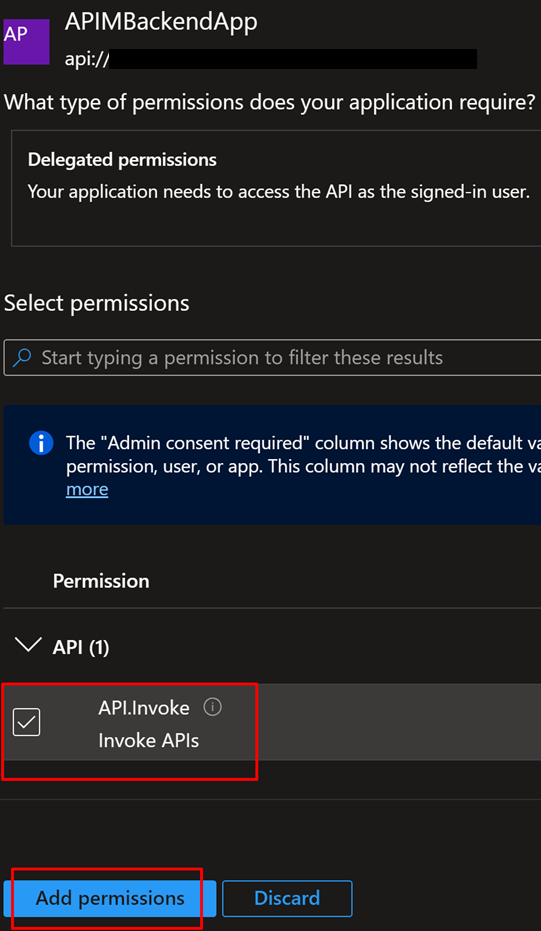
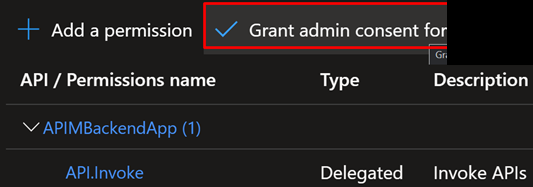
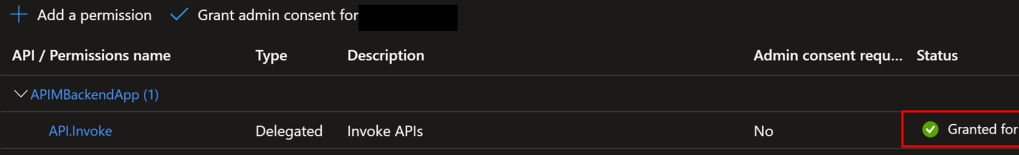
4. Grant admin consent for Default Directory
5. Now add a Secret and save it. Note – Secret value can’t be gained again, so keep it safe
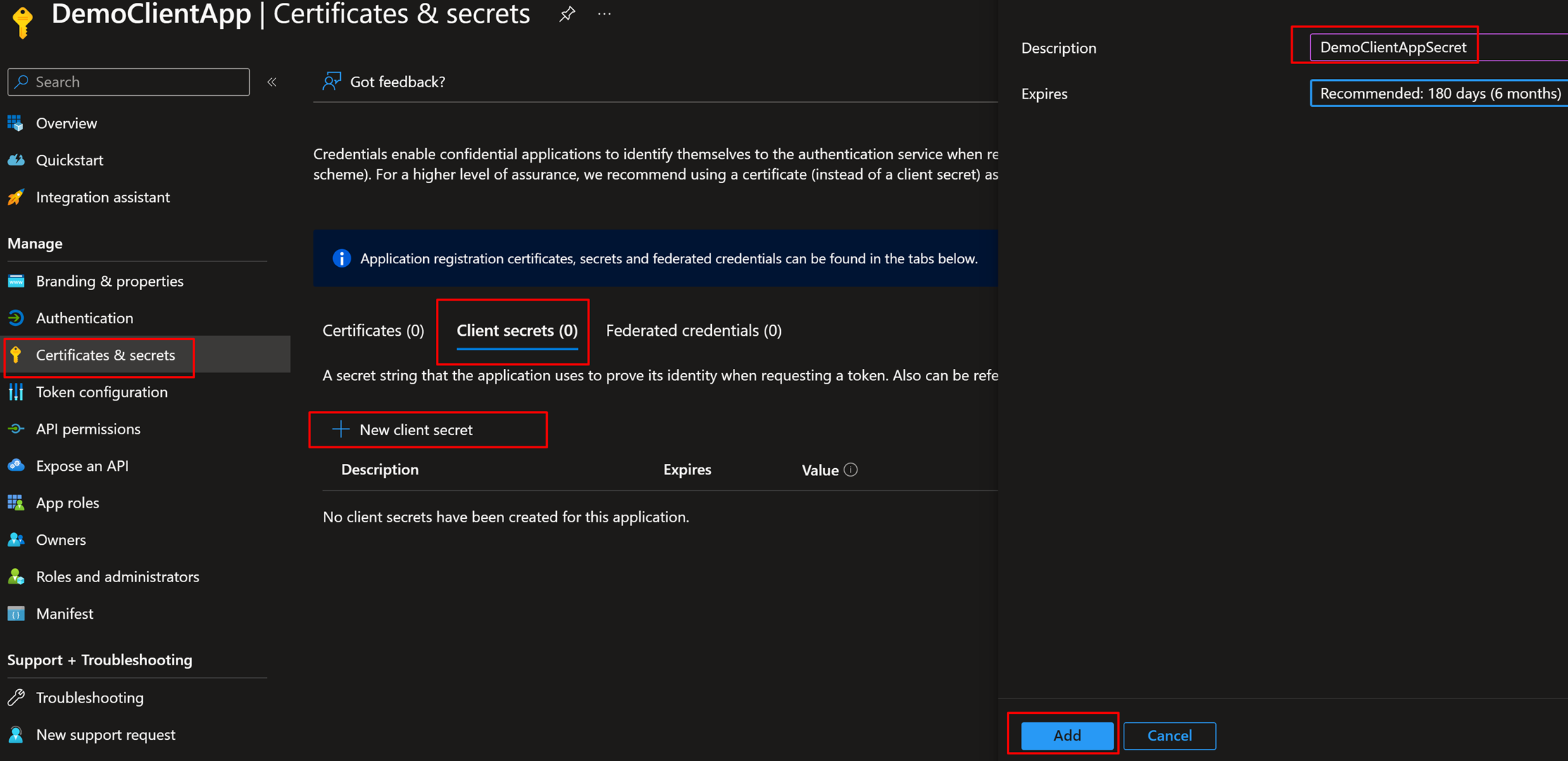
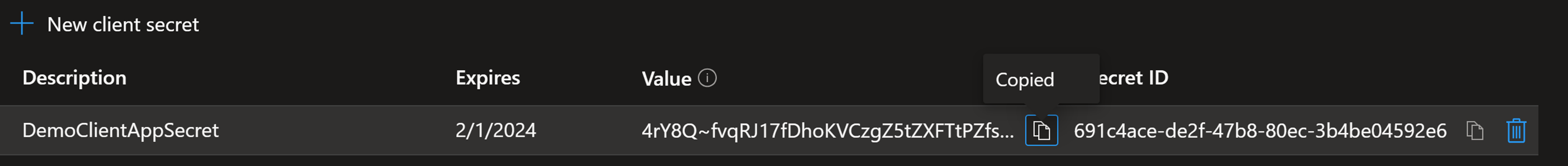
6. Make sure to also capture and save ClientID for this App
OAuth2 Service in APIM
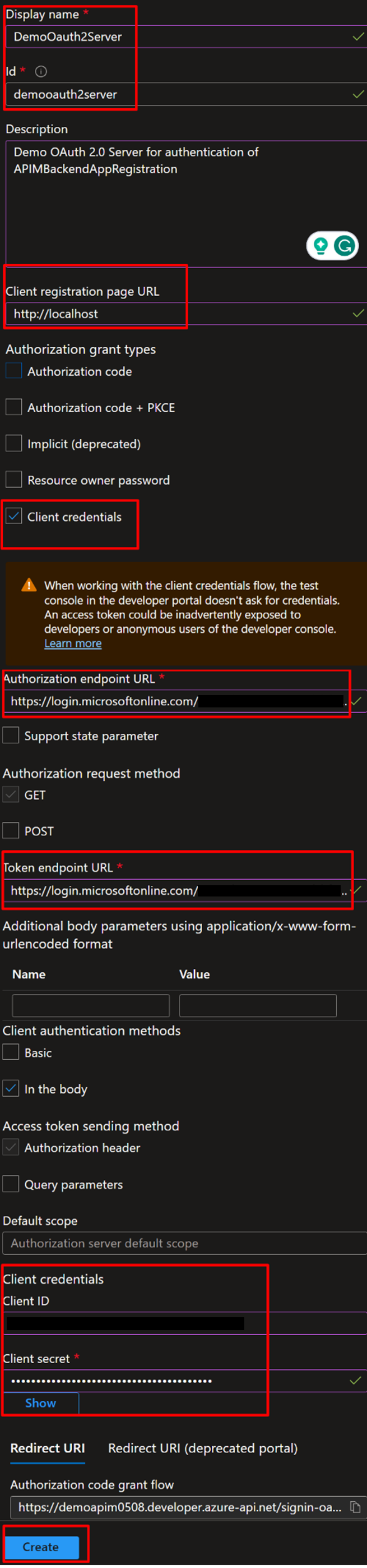
Now let’s create OAuth2.0 Service in APIM using details from App Registrations created above
- Go to OAuth 2.0 + Open ID Connect tab and +Add under OAuth 2.0
Details to be provided –
- Provide any Name and Description
- Client registration page URL as “http://localhost”(provided earlier in APIMBackendApp)
- Authorization grant type as “Client credentials”
- Authorization endpoint URL – Values copied from APIMBackendApp – “Authorization endpoint (V2)”
- Token endpoint URL – Values copied from APIMBackendApp – “Token endpoint (V2)”
- Client ID – Client ID of DemoClientApp
- Client Secret – Secret value created for DemoClientApp


Configure API Management API to use this OAuth Server
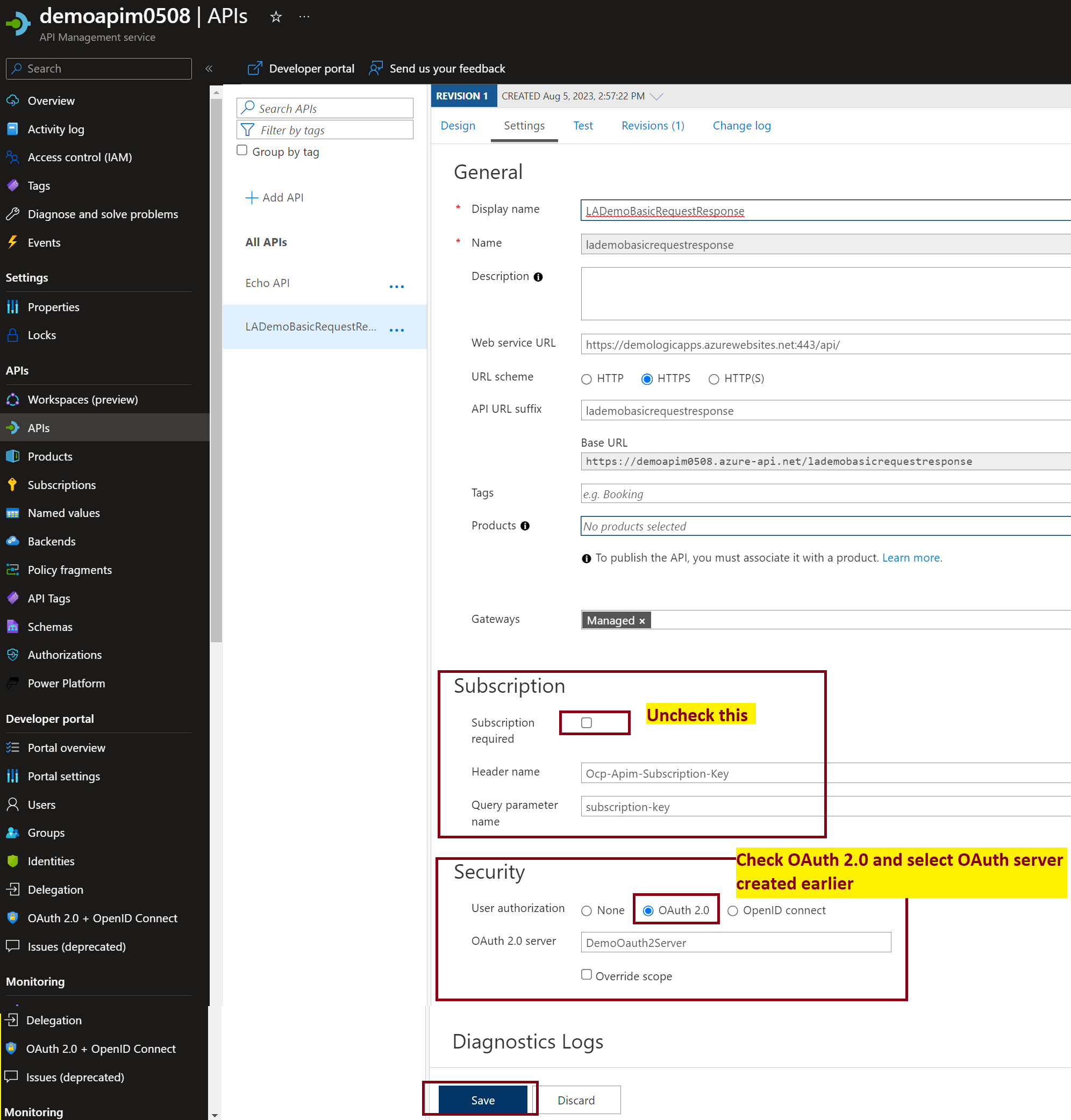
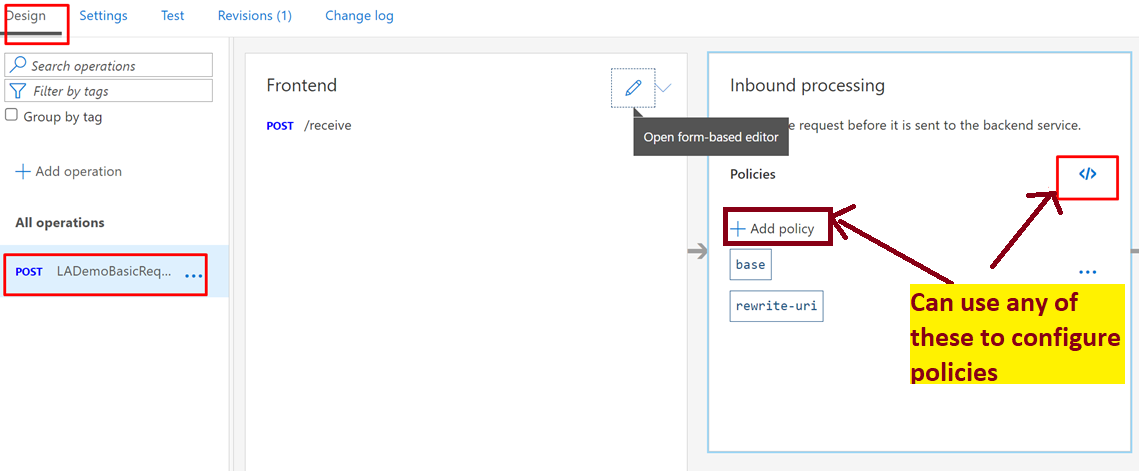
3. Now let’s create a few policies to enable OAuth to check during Inbound Processing
These policies can be created using UI way or directly in the form of XML
XML Representation – Make sure to replace TenantID and Client ID
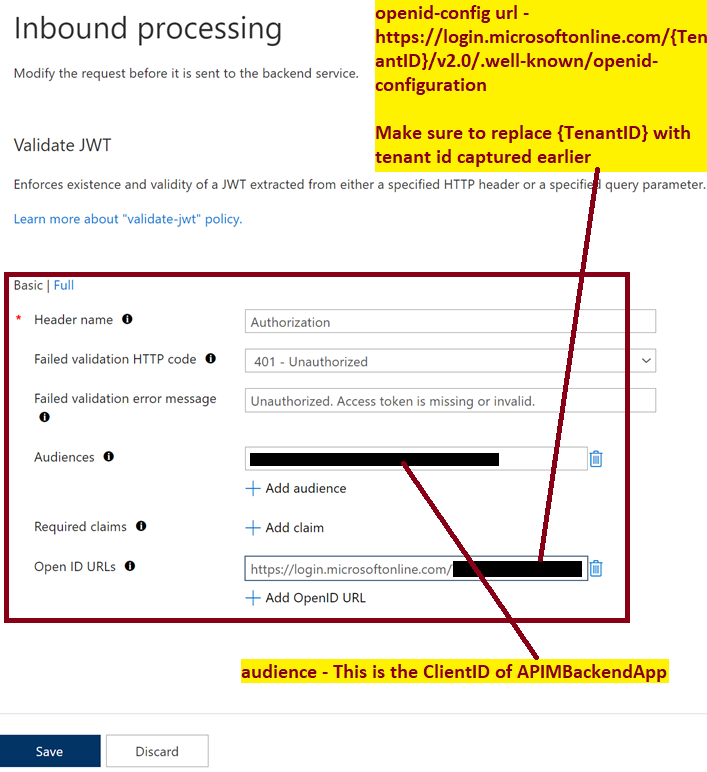
openid-config url –
https://login.microsoftonline.com/{TenantID}/v2.0/.well-known/openid-configuration
Make sure to replace {TenantID} with the tenant id captured earlier
audience – This is the ClientID of APIMBackendApp
<validate-jwt header-name="Authorization" failed-validation-httpcode="401" failed-validation-error-message="Unauthorized. Access token is missing or invalid.">
<openid-config url="https://login.microsoftonline.com/Replace With Tenant ID/v2.0/.well-known/openid-configuration" />
<audiences>
<audience>Replace with APIMBackendApp ClientID</audience>
</audiences>
</validate-jwt>
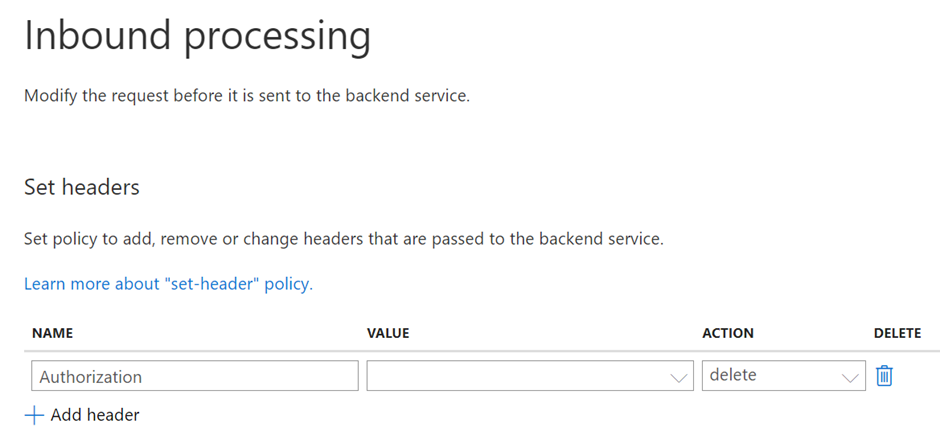
<set-header name="Authorization" exists-action="delete" />
UI Way of adding policies
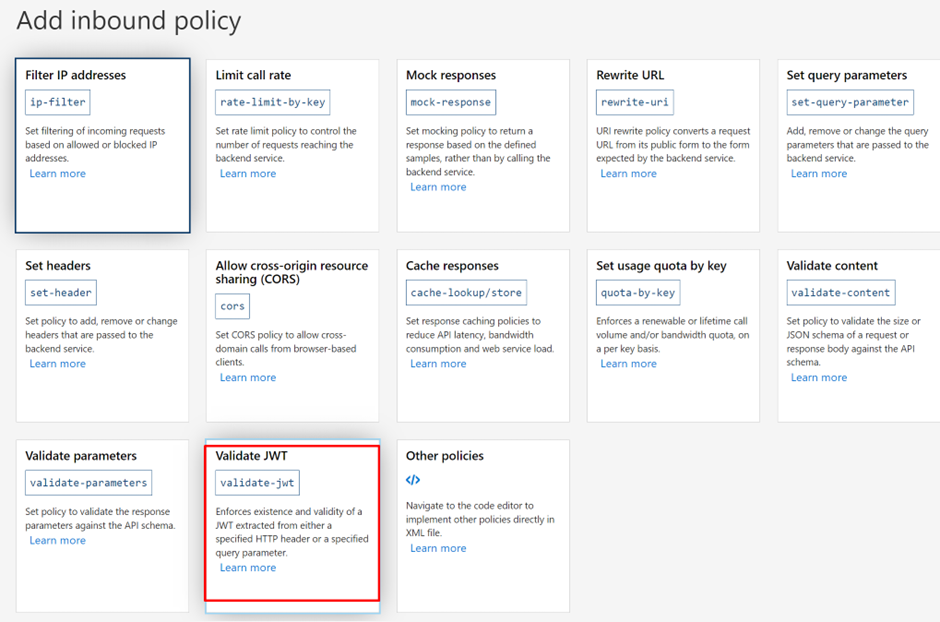
4. Click on Add Policy and choose Validate JWT
REMOVE AUTHORIZATION HEADER – This step is only required for Logic Apps as it expects only the SAS tokens and not OAuth token
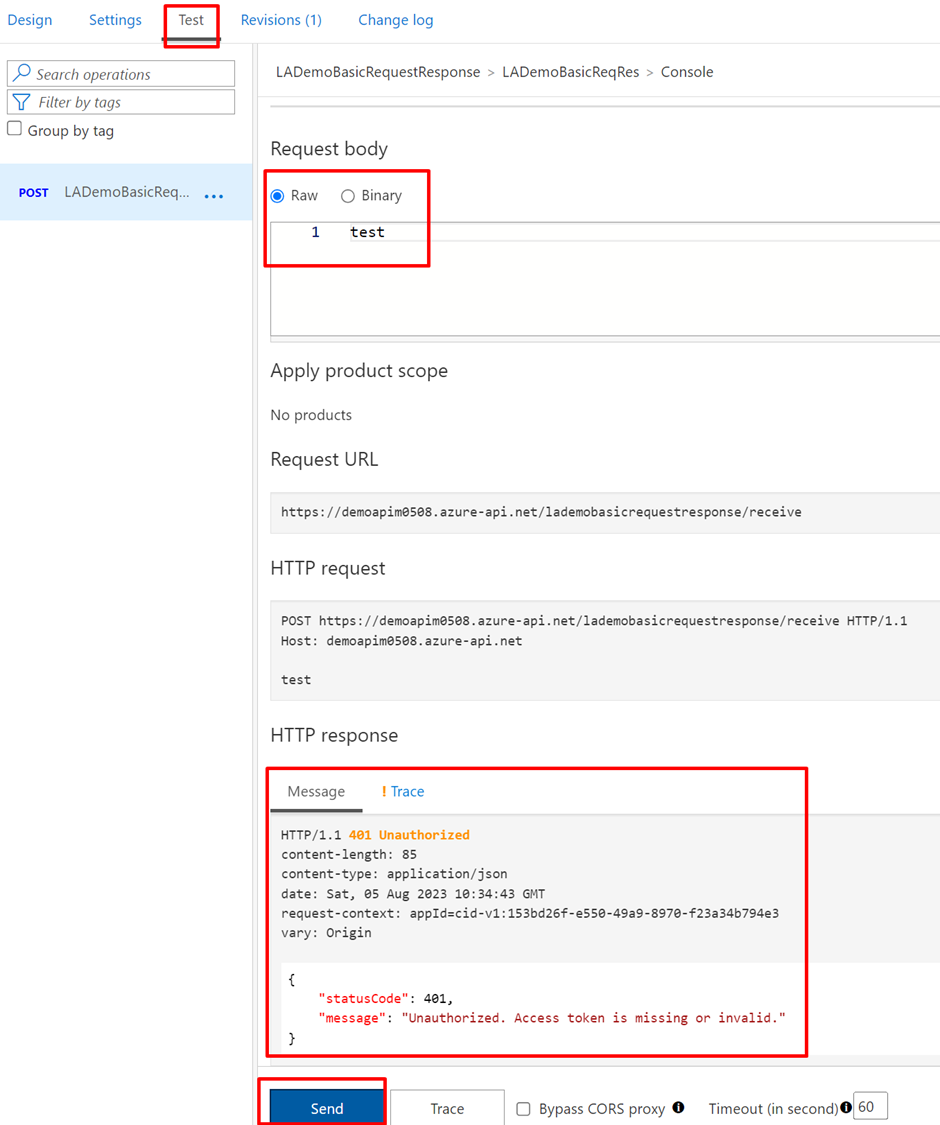
Now if you test the LA, it should throw below error –
Testing App using Postman
It has details from the App Registrations created earlier for APIM & Client
- Grant Type = “Client Credentials”
- Access Token URL = Token endpoint (V2) url from APIMBackendApp
- Client ID = Client ID of DemoClientApp
- Client Secret = Client Secret generated for DemoClientApp
- Scope = api://{APIMBackendAppClientID}/.default
Replace {APIMBackendAppClientID} with the APIMBackendApp Client ID
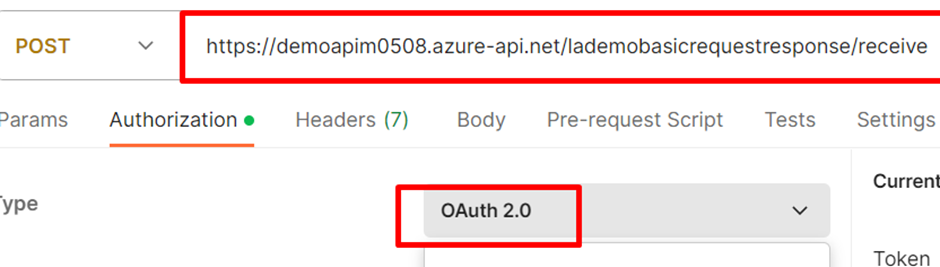
- Go to the Authorization tab in Postman and Configure New Token as shown




This concludes a successful test from the Postman. Share the same details with your clients who want to call this service.
Hope it helps.
Contact Me:-
@MyYouTubeChannel, @Gmail, @Facebook , @Twitter, @LinkedIn , @MSDNTechnet, @My Personal Blog
One thought on “Securing Logic Apps, Function Apps or Web Apps using API Management with OAuth2.0”